Regulatory insight on the challenges of strong authentication and SMS OTP
FACTS
- The ACPR recently reminded PSPs of their obligation to reimburse all fees related to unauthorized bank card transactions within one business day. This reminder also covers the legal framework for contesting this refund.
- The burden of proof relies on PSPs, and cannot rely on the simple SMS OTP to demonstrate their customer's negligence or fraud.
- Strong authentication for any online transaction must meet the security requirements of the RTS/DSP2. As a reminder, in addition to the EMV 3DS V2 protocol, the customer must be offered a two-factor authentication method, coupled with a dynamic authentication with a unique non-replayable code, transported from point to point in a secure way (so that it cannot be manipulated); in the case of a payment, it must be linked to the payment transaction (amount, merchant code).
CHALLENGES
- Strengthen trust in banks with interoperable payments in Europe, in a secure remote relationship through reliable and secure digital identity solutions.
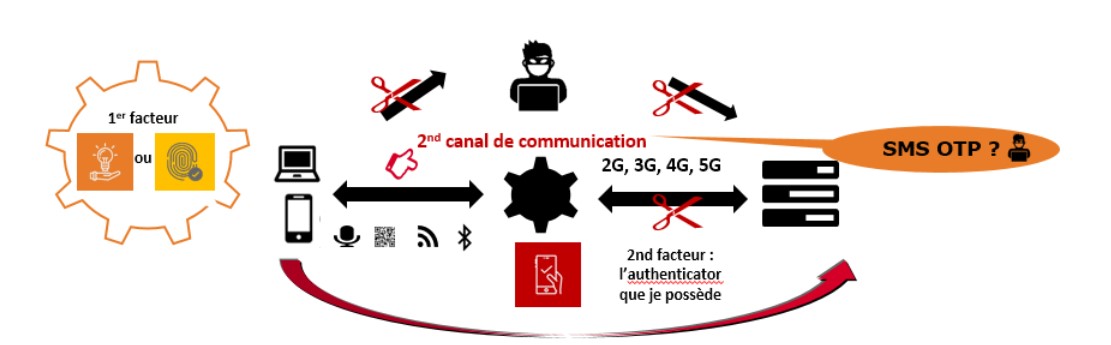
- Protect customers from any risk of identity theft and fraud, with strong authentication solutions that comply with RTS requirements, whether for access to their account (and therefore the initiation of a transfer) or for payment by card or any other means (transfer).
- Offer all customers alternative solutions to the simple SMS OTP corresponding to their online practices (Web, mobile), their acceptance and their equipment rate (with or without biometrics, mobile app or inclusive), without discrimination and without additional cost.
- Avoid any risk of customer dispute with their bank for a transaction validated by a simple OTP and this from the first euro (from May 15th 2021 in France).
MARKET PERSPECTIVE
- The legal status of the use of SMS OTP had already been the subject of an enlightened position by the European Commission: "Solutions should be based on the most secure authentication factors, moving away, as far as possible, [...] from older technologies and communication channels that are prone to attacks (e.g. SMS)"; but also by the EBA "which noted the insufficient integrity or confidentiality [of SMS] to be retained as proof of a reliable factor of possession".
- As with the unqualified electronic signature, the burden of proof with the use of SMS OTP is therefore on the issuer. But unlike the open legal framework for electronic signatures, which does not require a qualified signature, the RTS technical specification requires any issuer to have a report ensuring compliance with the requirements defined for strong authentication.
- In view of the difficulty of implementing the EMV 3DS V2 protocols and the associated exemption cases, but also to avoid the risks of abandonment due to non-optimized paths, the main schemes and legislators have tolerated the postponement of the RTS/DSP2 implementation deadlines and the possibility of continuing to use 3DS V1 with a simple SMS OTP as a means of authentication. Even in 3DS V2, some have chosen to continue with SMS OTP in addition to a second factor. But this tolerance will end in the coming weeks with the actual implementation of the soft decline.

- Even as a second factor of possession, SMS OTP must be secured to comply with RTS requirements; from an out-of-band channel point of view (SS7 transmission protocol) to avoid data disclosure and man-in-the-middle attacks, and to prevent the high risk of a hacker taking control of the smartphone (e.g. by following the UK Cyber Security Authority's guide)
- SIM SWAP protection is also a major liability issue for banks as well as for mobile operators or their resellers. Before being a payment fraud, it is an identity theft with personal data breach. In February 2021, the Belgian authority in charge of personal data protection sanctioned a reseller considering that he was responsible for the failure to protect the privacy of his customer with damaging impacts linked to this identity theft. In the United States, a crypto-asset investor also won his lawsuit against a mobile operator for a SIM SWAP that had caused him to lose $24 million in crypto-assets.
- No wonder in this context that three French operators (Bouygues Telecom, Orange and SFR) wanted to strengthen their SIM verify solution (SIM SWAP control initially limited to the recent change) by partnering with the American BOKU to identify with more certainty the owner of the mobile.
- BOKU's solution is mainly based on the analysis of fraud linked to call signals. However, is it sufficient and suitable for RGPD compliance? The debate is open and alternatives are emerging, such as the possibility for any subscription change to require a real identification equivalent to face-to-face, as with the French PVID specification for KYC, for identification for trust services or eIDAS digital identity.
